The following is based on my experiences and (limited) knowledge. I am not an expert in anything, nor will I likely ever be one. My hope is that this might help someone, somewhere, sometime. If nothing else, it might be a good start for discussion.
Preamble
This exercise is for educational use only, and is intended to be used in a lab environment, or as part of an authorized pentest. Please always ensure any scans or changes to systems are part of your pentest scope and comply with your rules of engagement.
The is the last in a series of of that walks through a fairly contrived example of how Metasploit can be used to exploit a client behind a firewall and from there be used to dig further into the network, with a final goal of remote desktop access to a Windows server. The purpose is not to go into great detail, but instead show the power of Meterpreter, its extensions and scripts.
Requirements and Background
Please review the previous posts. This lesson starts from where the part 4 left off. We have a meterpreter session and have just discovered a new subnet.
Process
Let’s explore the new subnet using the same process as before. We will type a ctrl-z from our meterpreter session to put in the background, and then add the new route
msf>route add 10.2.2.0 255.255.255.0 3
and then do a tcp scan. Interesting note about doing scans in metasploit, if you use CIDR notation (wikipedia Classless Inter Domain Routing) Metasploit will scan the broadcast address 255, which may give you interesting results.
We set up the portscan the same in part 3 and discover
[*] 10.2.2.191:139 – TCP OPEN
[*] 10.2.2.191:445 – TCP OPEN
[*] 10.2.2.191:3389 – TCP OPEN
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
While this scan was running, it might be a good idea to see if we can crack some of the hashes we gathered earlier, and find out what the password is. There are several tools available for this, but I generally start with John the Ripper. Maybe I’ll do a future series on some password tools, but in the meantime, I once again suggest you take a look at irongeek.com if you want more information right now
Using jtr, I was able to find out fred’s cleartext password, and from the above port scan, if fred has access to this server, we should be able to rdp into this server.
First back to our sessions
msf>sessions -i 3
Then we will setup a portfwd
meterpreter > portfwd add -L 127.0.0.1 -l 3389 -r 10.2.2.191 -p 3389
[*] Local TCP relay created: 127.0.0.1:3389 <-> 10.2.2.191:3389
Explanation
Portforward can be used to setup a “proxy” tunnel between you and the machine with the Meterpreter session. portfwd has the following options
-L
-h Help banner.
-l
-p
-r
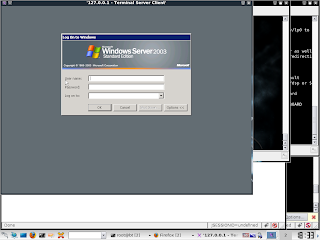
Now, on your machine, you can open up rdesktop, or whichever remote desktop tool you use, and in the server to connect to address type in 127.0.0.1 (if you did not use 3389 for the port, enter it as well).
Remote desktop will connect,
Next Steps
This is the last post in this series, but it is not the end of the test. As darkoperator says = shell is the only the beginning, and there is much more that can be done post-exploitation.
My hope is to use the systems in this series of posts to explore Metasploit and other tools in future posts.